In my Monday Morning Cup of Coffee post this week I included pictures of two emails that I received this weekend. One was immediately obvious to me that it was a phishing email and the other required further investigation. So which was the phishing email? <insert drumroll here>
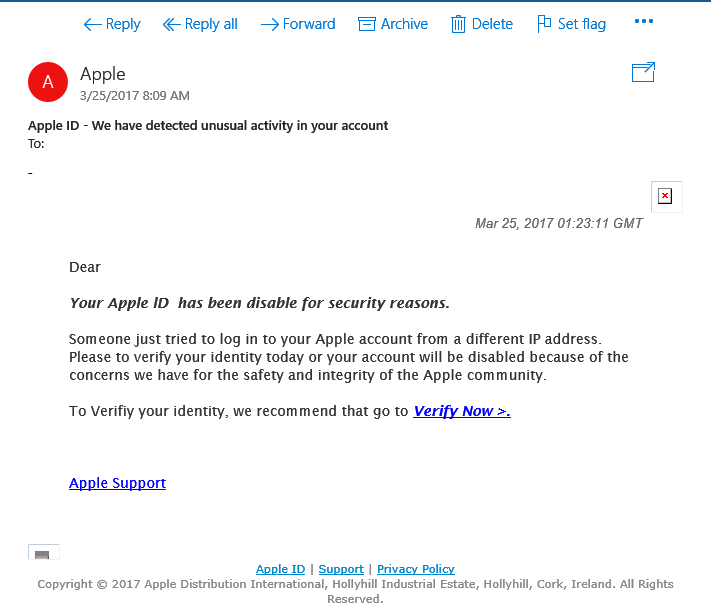
The "Apple" email was the fraudulent email.
The way that I instantly knew that it was fraudulent was the spelling, grammar and capitalization errors. These types of emails are always sent from an automated system and an established company like Apple would not have spelling or grammar errors in an email like this. Also, if you examine the links before clicking them, you can see that the link is not directing to the Apple site:
In most email programs on a PC you can just hover the mouse arrow over the links without clicking them to get a popup (above) of where the link is sending you. As you can see from the example, it was not going to send me to anything at Apple.com but rather to the strange link shown. It's a very common deception tactic to make a link look like it's going one place but have it redirect you somewhere else. For examplie:
See what I did there? :-)
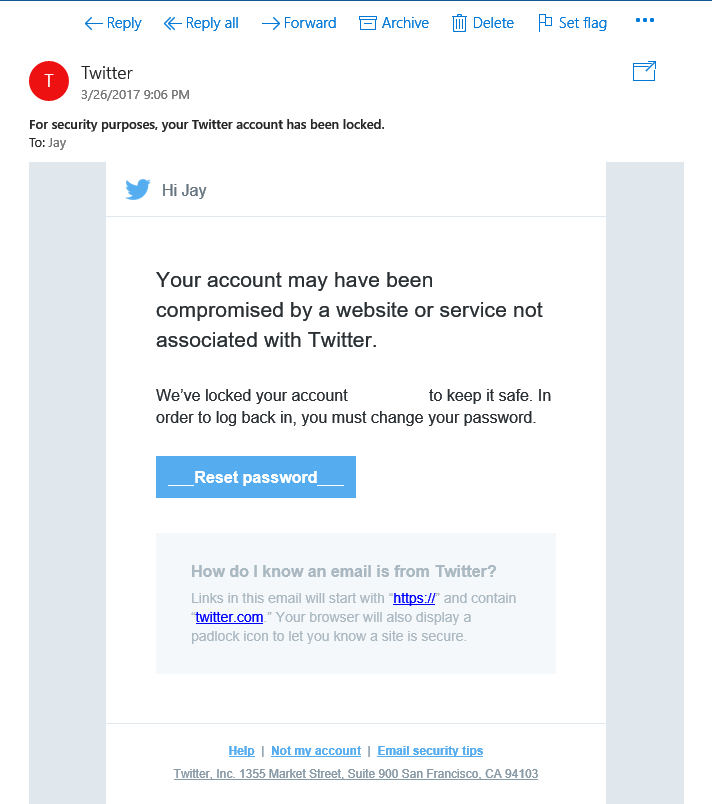
The second email from Twitter was not so obvious to me and as @DellRabinowitz pointed out on LinkedIn, both emails seemed suspicious.
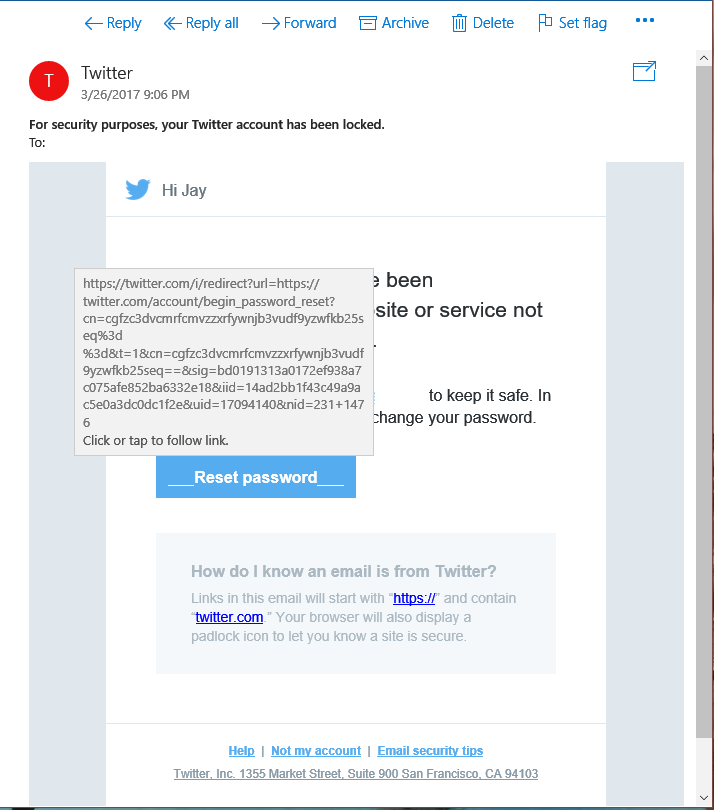
There are no errors in this email. However it didn't quite render properly and I was suspicious of the visuals of the "Reset password" button. So one again, I checked the link:
In this case, the link address (though long and confusing) is actually going to the twitter.com domain. I still dug a bit further because of the length of the URL but ultimately this email turned out to be legitimate. There are several strategies to combat this deception but here are a few quick tips on how to stay safe from these types of attacks:
- Check the link addresses before clicking them. I would recommend doing this for most links contained in emails, even if the email seems to come from a trusted person or brand. One a PC or Mac you can generally do that by hovering your mouse pointed on the link without clicking it. On Apple mobile you can long press on the link to display the address without
- If it's a "reset password" or "security compromised" email, go directly to the site in question without clicking any links. For example, going to Twitter.com and attempting to login with my current credentials revealed that my Twitter account was indeed locked out.
- Copy and paste the link into a tool such as Norton Safeweb or ScanURL. These services check the links that you paste into them in order to verify that they're safe.
- Stay vigilant! If an email is asking for a password or sensitive information be especially careful with it. If it looks like it's from your bank or credit card company, a phone call to their fraud department may be in order. It can be a hassle to call them up front but it's definitely better than accidentally exposing information and having to call them after the fact!
If you have any questions, comments or would like to know more about the seven layer security model that NeoCloud Consulting provides for our customers, please contact us!
Semper Vigilis!
--Jay